George Orwell was right — invasion of our private lives is becoming a greater threat with each passing decade. Even if it’s not being used by Big Brother’s totalitarian regime, our sensitive information is increasingly accessible to unscrupulous corporations, cybercriminals, and anonymous strangers who know where to look. According to Wikipedia, “Doxing or doxxing is the act of publicly revealing previously private personal information about an individual or organization, usually through the Internet.” It’s an increasingly common act of intimidation and an exposure meant to enable complete strangers to actively engage in harming you.
In 2012, an interactive map was posted online showing the names and addresses of New York handgun permit holders in Westchester and Rockland counties. Was this freedom of the press or potentially endangering people? Whether those gun owners like it or not, their info is now exposed, even if the post is deleted. More recently, the web site for the California Department of Justice leaked personal information — including full names, home addresses, dates of birth, and whether the individual works in law enforcement — for thousands of the state's gun owners. The President of the California Rifle and Pistol Association called this a “vindictive” act by “sore loser bureaucrats,” implying that it may have been a response to the recent Supreme Court ruling that forced the California DOJ to remove its “good cause” requirement for concealed carry permit applications.
The list of similar situations goes on. From the dentist who shot Cecil the Lion, the Ashley Madison data breach, or celebrities Tweeting out the home addresses of people they don’t like, one thing is for certain — the more information you have online, the greater the risk of it being used against you. If you were part of a group that’s becoming increasingly stigmatized — and you may already be without knowing it — how can you protect yourself from the prying eyes of the outrage culture zealots who mean to harm you?
The Doxing Scenario
Situation Type: You’re being doxed
Your Crew: You, your wife, and your children
Location: Your hometown
Season: Autumn
Weather: Normal
The Setup
Imagine you attended a city council meeting to express your concern about the side effects of a growing homeless population in your area. You plan to voice concern for your family’s safety after witnessing an increase in drug sales, sexual assaults, and public defecation. This meeting is packed with people on both sides of the issue. Some activists who attended this meeting did so in an effort to retaliate against residents who were speaking out against the homeless problem. While attending, they photographed attendees, got names and addresses off the sign-in list, and used public social media posts and press photos to identify the key participants in the meeting.
Also, an online petition appearing to solicit residents to push for legislation that imposes tougher penalties against homelessness had recently been started. By the time the petition had reached several thousand signatures, including your own, it was determined that everyone who’d signed up had been catfished. The fake petition was actually started by a self-proclaimed social justice blog that published all the names, addresses, phone numbers, and personal info for the world to see. The blogger didn’t openly condone violence, but encouraged his followers to go “have a conversation” with everyone on the list to teach them the error of their ways.

Illustrations by Joe Oesterle
The Complication
Now hostile notes are being left in your mailbox, harassing calls and texts from blocked numbers are coming in, and you genuinely fear that the reprisals will become physical. How can you protect yourself against open-source information collection, harden your digital footprint, and mitigate risk without abandoning technology altogether? We asked tactical trainer Katheryn Basso and financial industry expert Dennis Santiago to weigh in with their recommendations on how to stay safe when revenge-driven people are targeting you based on what they can find on the internet.
Tactical Trainer Katheryn Basso’s Approach
I used to take a lackadaisical approach to my internet and phone habits. I kept my location services on 24/7, connected Google to everything, and handed out my personal data and contact information to any account that needed it. After all, I had nothing to hide. In fact, I figured if something were to happen to me, maybe it would help the police locate me. Unfortunately, in today’s divisive climate where your beliefs, hobbies, or actions may offend the wrong person, limiting your internet footprint is vital to privacy and safety. In today's environment, Internet Doxing can quickly lead to real-world dangers.
As memberships and access to even the most mundane interests become digital, the threat of your information falling into the wrong hands increases. Your hacker could be a 13-year-old boy just testing his latest Kali Linux skills, a highly sophisticated cybercriminal who makes a living off blackmail and extortion, or a violent person looking to harm you. This anonymity makes it difficult to identify and prosecute the perpetrator — you may never know who is committing a crime against you, or why they’re doing it.
You may be surprised how much of your information is already available to the public, just waiting to be used against you in some hateful campaign. However, it’s not too late. With some dedicated work, you can increase your privacy and lessen doxing damage before it occurs.
Preparation
Let’s first call out the biggest issue: I gave my true name and real address to an unverified online petition. Let’s say I wasn’t thinking straight and slipped up. That’s fair; it happens. In this particular situation, I assumed the petition going around was for government purposes: gather enough signatures of actual residents to push for legislation change. Most of these online petitions require personal information (full name and address) they ensure will remain “safe” within their site. In order to properly arm myself from doxing, I need to change my thinking. I need to assume a data breach will occur at some point with every online site.
I’m sure you think that’s extreme, but I was in the military during the Office of Personnel Management breach. If 4.2-
million current, former, and prospective federal employees’ background information can be stolen, how secure do you think your information is at the local coffee shop? Is that free coffee for joining their mailing list really worth it?
One free and easy way to see if your email address and/or phone number were part of a breach is to check them at HaveIBeenPwned.com.
Unfortunately, in today’s age of connectedness, digital marketing, and data analytics, most businesses and sites require a name, email address, and/or phone number to access member-only benefits. So, how can I live in today’s age of loyalty points, travel rewards, and grocery shopping discounts while also remaining as safe and secure as possible? I should assume I’ll be exposed, then take a few general security steps to mitigate the breach.
1. Remove my information from data aggregates: Third-party data mining companies have been collecting my publicly accessible information since I got my driver’s license. This includes addresses, phone numbers, email addresses, known associates, etc. The good news is I can request they remove my personal data from these sites. This is a long and tedious task, but I know it’s worth it to gain control over my security. Check out Michael Bazzell’s IntelTechniques.com for a helpful list of data-removal options.
2. Opt for a credit freeze: Putting a freeze on your credit prevents identity thieves from attempting to open new accounts (i.e. credit cards and loans) in your name. A credit freeze doesn’t prevent you from using your current accounts. You can unfreeze your credit at any time, and it’s absolutely free. Freeze your credit at each of the three main credit bureaus.
3. Use various junk email addresses: I use multiple email addresses for my junk email — those accounts that require an email address for access. I rarely check these accounts since I know they’ll be sold to third-party companies for marketing. Since these accounts are usually part of breaches and aren’t tied to important accounts, any follow-on phishing attempts are easily spotted.
4. Create strong passwords: Most of these breaches include email and passwords. I use a secure password manager that creates strong passwords for my accounts. If you asked me what my password was for any given account, I wouldn’t be able to tell you without going into my password manager. I highly recommend you use unique passwords for each account and update them every 60 to 90 days.
5. Use a VPN: A Virtual Private Network secures your connection by creating an encrypted tunnel between your device and the website you’re visiting. This not only prevents hackers from intercepting your data, but it also masks your Internet Protocol (IP) address so your activities cannot be traced back to you. Compare VPNs before you purchase; they are not all created equal.
6. Use VOIP phone numbers: My phone is constantly talking to cellular base stations that could be used to triangulate my location. While these services are restricted to authorized personnel — like law enforcement and bounty hunters — they aren’t 100-percent safe from the human factor (disgruntled employees, assistants wanting to make extra cash, or hackers). Google numbers or paid Voice-Over-Internet-Protocol numbers provide an extra layer of security between yourself and nefarious individuals. I hand out a VOIP number when required to provide full contact information. And if one of these numbers gets compromised, I can easily switch VOIP numbers without the hassle of changing my true number.
7. Encourage security habits with family and friends: Those closest to you tend to be your weakest link when it comes to securing your privacy. Again, most people don’t think about their own physical security when they’re safely behind their phone or computer screens. While social media has provided us a way to connect, it’s also a treasure trove of open-source information that can lead people to your location. How much you restrict on social media is a personal choice — I know many people who refuse to have accounts. However, you can’t always control your friends and family. I tend to have a 24- to 72-hour rule with social media; I upload pictures one to three days after an event. My friends or family, however, may upload a picture of us immediately. There’s not much you can do except avoid pictures or ask them politely to wait or remove the image. Encouraging your friends and family to follow your privacy habits may not always be easy, but it’s worth the conversation.
8. Encourage security habits with your neighbors: While the same privacy-minded habits can and should be pushed with neighbors, physical security habits are just as important. After a few scary incidents here, an active neighborhood watch, security cameras and trail cams have proliferated through the community. Deterrence is important to maintain physical security, especially if one of our addresses is posted online for nefarious purposes.
Crisis
Now that I’ve taken certain privacy precautions, let’s return to the scenario. My name and address have been released online. All that work was easily compromised by one single mistake, yet my preparation has prevented a bigger disaster. Yes, they know my address, but my emails, accounts, credit, and passwords should still be safe. So, what are the next steps?

1) Get the police involved. Take a screenshot and report this to the police. Most states have some form of anti-harassment/anti-stalking laws that cover doxing situations. Do note, even if they’re able to take the site down, it doesn’t prevent the wrong people from obtaining my contact information. It’s out there now; it can be continually republished as long as there’s still a will to create harm. Thus, I’d request extra police presence; ask them to drive by my house as part of their rounds. Again, deterrence is important. Due to limited staffing, this may or may not be possible, but I can ask. Since I have security cameras, any physical trespassing will be caught on tape. I can provide this to the police as well to assist in their investigation.
2) Change my number. Luckily, I provided a VOIP number that can easily be changed. If, for some reason, my real number was leaked, I’d cancel that plan, get another phone, and start using a different VOIP number. Get clean first.
3) Become physically secure. Depending on the level of threats, I’d have to decide whether to stay at my residence, leave my house temporarily, or permanently move. This is a huge decision based solely on the danger and my willingness to accept risk. Often with these doxing situations, threats subside once the perpetrators move on to their next cause.
I, like most people, have Googled myself. Now that I’m writing in true name and taking part in interviews, I am becoming more exposed in the public sphere. I’ve chosen a level of security that fits my goals and lifestyle: I want to exist, but not necessarily be found. The steps outlined above are a few basic privacy measures that’ll assist you in living safer in a digital age; they are by no means all encompassing, nor will they set you up for extreme privacy.
Financial Industry Expert Dennis Santiago’s Approach
You wake up to a nightmare. Out of the blue your privacy has been stripped away. It’s all because you said something, wrote something, or participated in an action that you believed was moral and ethical. You expressed your opinion like a free person in America has the right to do, but an organization of strangers didn’t like it.
And now you’re asking yourself three questions: What could I have done to avoid this? How do I make this end? What needs to change so it doesn’t happen to others? We’ll break that down, but first a little insight to let you know what you’re up against. This is vile, asymmetric warfare.
For instance, you’re probably aware of the term “Facebook jail,” a sort of purgatory for your residual self-image in the matrix of the internet. Anything you say on social media can result in anonymous complaints being filed against you. Your accounts become increasingly restricted, if not hacked and vandalized. You don’t wind up there by accident. Somewhere out there, strangers are accusing you of being a witch, turning in complaints, and asking the algorithms, moderators, and reviewers of the web to burn you at the proverbial stake.
That harassment also follows you to your workplace. The barrage of phone calls and emails affects you there too. Like the complainants on social media, this army of strangers are demanding you be fired. The company you work for goes into a panic because they’re in the headlines for all the wrong reasons. In some cases, your career may tumble out of control or come to an end.
Politically outspoken people who exercise their 1st Amendment right to free speech are particular targets of this sort of harassment. Doxing doesn’t care who it hurts. It can be for any cause. In this age of the tiniest thing triggering nuclear retaliation, you could’ve said you didn’t like wearing a mask. On the internet, someone will be angry enough to take offense; and where there’s one, there’ll be many more. And some of them will be vicious.
What could I have done to avoid this?
The first thing to realize is that doxing is a very personal version of psychological warfare. It’s very much an antisocial and cowardly act by one human against another. If it’s done to you, the people engaging in it are actual enemies. They’re seeking to exploit your vulnerabilities to intimidate you. They’re out to silence you by whatever means they can. What you need to do is minimize your target profile.
The second thing to realize is that there’s no such thing as anonymity on the internet. Many people use pseudonyms. Such a practice almost always eventually gets you into trouble. It’s fun to come up with a catchy name for yourself and immerse into a role-playing persona with the anonymity of a pen name. You express thoughts standing on a soapbox from inside what feels like a cocoon of anonymity. This makes people brave, sometimes enough to take extreme edges of the argument. This is all but guaranteed to raise the ire of those who hold opposite views.
Before the internet, it was difficult for these opposing parties to find each other in the real world. Conflicts were avoided simply because the pairs of volatile personalities would never meet in real life.
With the internet, that barrier to interaction is gone. Billions of people can have access to every musing you express on the medium. And if they don’t like you, they’ll take note of you, not because of who you are, but because of the ideas you represent. Ideas they hate. When doxing perpetrators attack, they’re hoping the revelation of secret identity will be enough to silence the target. Avoiding an attack in the first place requires you manage your vulnerability.
First, consider not being anonymous in the first place. Being yourself in the universe of debate means there’s nothing hidden to expose. It’s taking the high ground with your opinions. Revealing who you are when you open your mouth forces you to heighten your awareness of the consequences of what you say. They can’t expose what’s already in the open.
Second, curate who you interact with. Engaging in politics with strangers is a dangerous thing we humans do to each other. Online, remember to trust no one. Do your homework and check out every person who tries to come into your orbit.
Did that person actually say they believe that anyone who’s hesitant to be vaccinated should be “compelled” to do so or be banned from participating in any social activity? Did you see that person comment to someone else that they actively report persons they don’t agree with politically to the social media platform’s anonymous complaint utility?
Situational awareness is something most people interested in their survival and happiness should practice. Detecting persons with dangerous antisocial traits who act on those impulses is one of those recognize-from-afar things. It’s OK to mute friends who’ve become hyperactivated by spending time in too many echo chambers. I now do that at the onset of political election cycles. It’s better for preserving friendships based on enjoying what’s common and tolerating what isn’t.
When I detect people who are truly dangerous, I just block them. I use the harshest protective tool available on the platform, and make sure I can’t see them and they can’t see me. The technical term for that in electronic warfare is “interrupting the firing solution sequence.” It’s really hard to click on the report-this-post option on a social media platform if that person can’t see the post in the first place.
I’m not saying entirely avoid people who have colorful personalities, or those who have differences of opinion. That’s silly. Our ability to live within a culture of independent citizens depends on our ability to tolerate each other. You’re just trying to winnow the psychos, which is a prudent thing to do as far as I’m concerned.
Third, take the time to realize that every action you take is self-revealing, like a walk through a minefield. It’s important to know who’s real, who’s a fake personality, and what’s an artificial intelligence robot (those can now emulate humans very well indeed). They’re out there on the internet. You’ll run into them if you actively discuss current events and politics. They aren’t there to discuss things. They’re there to trigger to you discuss things and demonstrate subject matter affinity that they can sell as marketing data to other companies on the internet.
It also could be as simple as ad revenue being the motivator — every digital news bureau and all their clickbait-packaged stories are all about making that top-line fraction of a penny each time they get someone like you to look. On the internet, the money has always been about the commercials, the ads that get served along with the stories. If you choose to involve yourself publicly in these issues, it’s important to stay aware of this. When you post or repost a story, meme, or article, you’re revealing a piece of research information about yourself. Hundreds of algorithms go to work on that information a microsecond after you click “send.”
Fourth, curate yourself responsibly. There’s a concept of how you comport yourself in public and in private that’s important to manage when interacting with the world on subjects that can trigger other people to take offense. My advice here is that what you say in public should always be measured. How you ponder the extreme ends of the spectrum of possibilities should always be private. What position you finally come up with should be a balance between emotion and reason. It’s good to take the time to research your opinion to see where it falls in the spectrum of society. Too many people think the privacy of what they type into a keyboard while alone late at night is profound, and then the sun rises in the East. Don’t be that guy.
Fifth, don’t fall into the trap of trying to be the most popular person in the room. There’s a macabre thrill that comes along with seeing what you’ve said explode virally into thousands, or even millions, of likes. It can be addicting to chase popularity. The internet beguiles with tales of riches for people who have turned the corner curating themselves into a money-making operation. But for a person selling nothing but their opinions, it tends to be a chase that ends in anguish. Eventually you’ll fly too close to the sun and your wings will melt. The most important people in a room have an aura that’s easy to spot. They’re just quietly there. They aren’t the ones jumping up and down yelling, “Look at me!” You don’t have to be one of them either.
How do I make this end?
In this case, whether you did or did not abide by the vulnerability management things listed above, you got doxed anyway. Now what? You’re in crisis mode. First, start limiting the damage. Change all your passwords and screen names. Review all your contacts and cull anyone overtly hostile. You just hit a moment on the internet where it’s better to have a few trusted friends than thousands of acquaintances. In the worst case, suspend your accounts, if there’s an option to do so.
Second, if the harassment becomes physical, don’t ignore it. Put up “no trespassing” signs at your property boundary. If it’s bad enough, change your phone number. Get a new email address. Put up multiple high-definition cameras and record everyone that comes to your doorstep. If you can, add additional cameras that record the license plates of cars coming and going. Do this until the hoopla passes. Then, you can consider going back to normality.
Third, deal with the consequence effects of being doxed. If you were using a pseudonym to hide your identity to participate while throwing flaming bombs yourself, you may now have a price to pay in the real world for having done so. That’s a risk you took. That’s a price you must be prepared to pay. I haven’t found anyone who’s done this and never had to face the day it blows up in their face. Karma. It’s real. Back to my advice, “Don’t be that guy.” But if it did happen, I have another piece of advice that’s seen me through many trying times, “Sometimes the only way to win is to lose gracefully.” That may be what you need to do. For your family’s sake, do what you need to do.

What needs to change so it doesn’t happen to others?
The thing about doxing is that your attackers are also ones hiding in the shadows of anonymity. I believe that’s the beginning from where society needs to mount a counterattack. Current laws and abuse reporting policies tend to protect the anonymity of whistle blowers. The problem is that these protections apply even when the whistle blowers are actually malicious witch hunters.
It’s not like the social media companies don’t have records of who made the complaints against you. Users’ emails and IP addresses are retained, and the presumed anonymity of the accusers can be pierced if malice is revealed. Artificial intelligence algorithms to test for maliciousness and abusive reports can be designed. Tech companies can scrub the internet to halt a viral contagion from propagating, or to manage a political war, as we saw in 2020. The problem is that none of these systems are being used to protect the maliciously accused from frivolous attack, particularly when it comes to real-time solutions that follow the principle of innocent until proven guilty. In corporate America, risk management is designed around the exact opposite principle — the accused is in the wrong until cleared. The technologists and the legal departments that advise them should probably be pushed to get those principles into a better balance.
It’s not that these detectors are hard to make either. Patterns of abuse tracking are certainly part of determining whether to put a user into virtual “jail.” Why not use patterns of abuse analysis to detect serial abusers of other people’s right to have an opinion? It’s similar to the process of hunting pedophiles online. It’s time to stop enabling abuses by the witch hunters.
To be sure, such an abuse-catching system would find bad behavior across the entire spectrum of opinion in America. The internet’s technology and legal framework design enables the problem. But is it so bad that everyone will have to learn to behave and be more civil while exercising the 1st Amendment?
Conclusion
Anyone can be doxed. Even if you avoid social media, use a VPN, two-factor authentication, firewall, and password manager to hold each unique password for each unique secure email account from a non-attributable computer or phone, you can’t control the human factor. This isn’t just a cyber issue — it’s a life issue. And if you plan on getting involved in your community, your children’s school fundraiser, or your work’s outreach program, there’s a chance your information, such as a picture of your face and contact information, could be released to the public. That’s a part of the world we now live in.
However, taking precautionary steps to limit exposure could prevent an event like this from becoming a nightmare. Security isn’t always convenient; it’s not always easy. But considering the alternative, it’s worth it. You choose — the life of an antisocial mountain hermit or existing in the real world with certain inconvenient steps to ensure privacy.
About the Authors

Katheryn Basso
Katheryn Basso is a U.S. Marine Corps veteran trained in identifying sources of instability in foreign countries. Proficient at navigating the complex civil-military terrain of foreign policy, she has advised and advocated for military and civilian leaders from multiple partner nations. She’s currently the co-owner of TEAM TORN, a tactical training company based in Nevada that instructs U.S. military, government, and civilian personnel. She specializes in firearms instruction, conflict avoidance, and personal security strategies. www.teamtorn.com

Dennis Santiago
Dennis Santiago is a global risk and financial analyst. His national policy expertise includes strategic warfare, asymmetric warfare, and global stability. He’s a financial industry subject matter expert on systemic risks to the U.S. economy and the safety and soundness testing of U.S. banking institutions. www.dennissantiago.com
More Scenarios to Consider




 Above: An Atpial-C has the same form factor as a PEQ-15, but without the same output.
Above: An Atpial-C has the same form factor as a PEQ-15, but without the same output.


















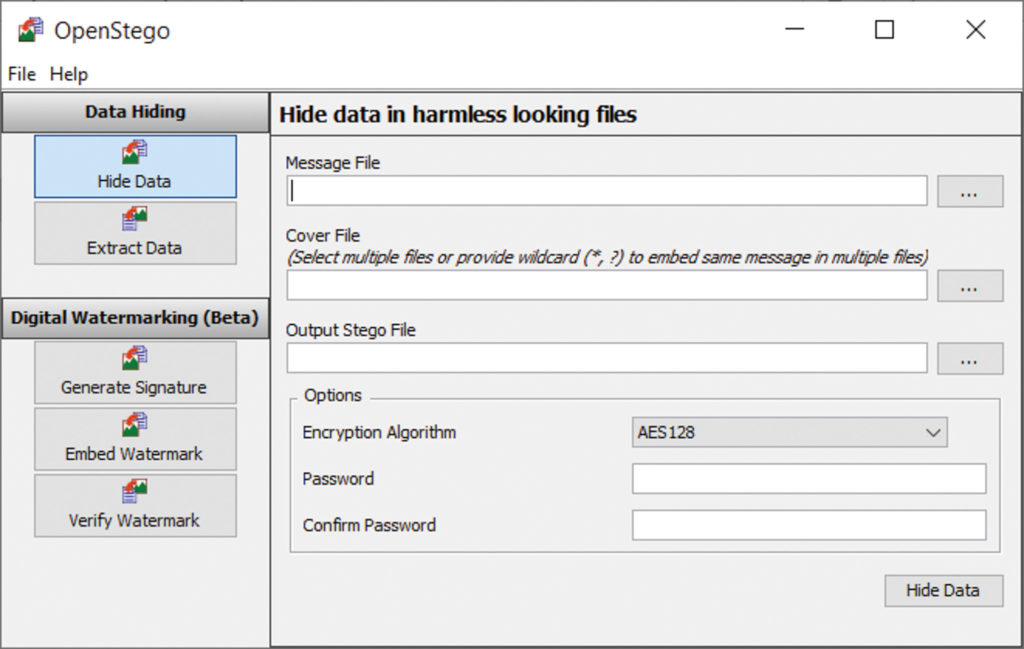
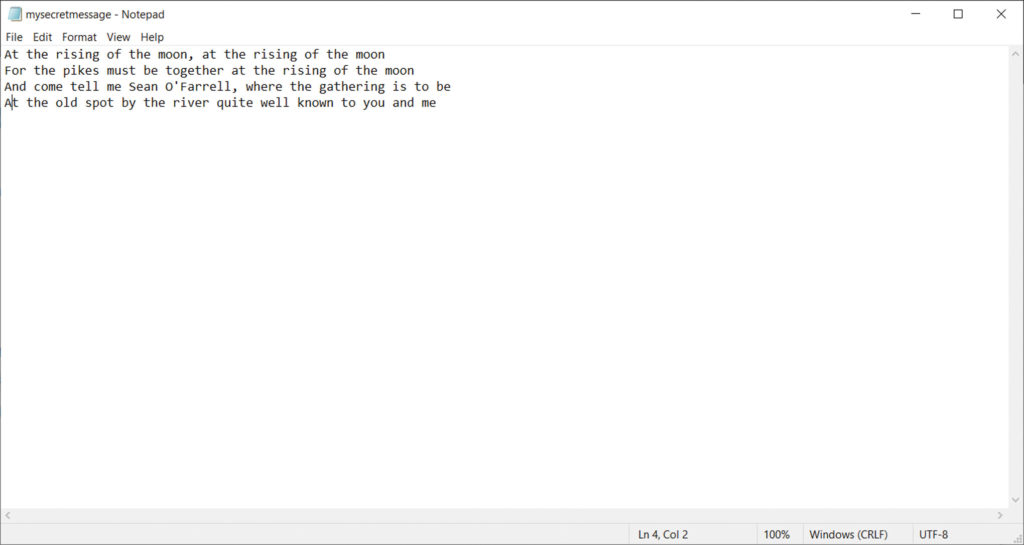
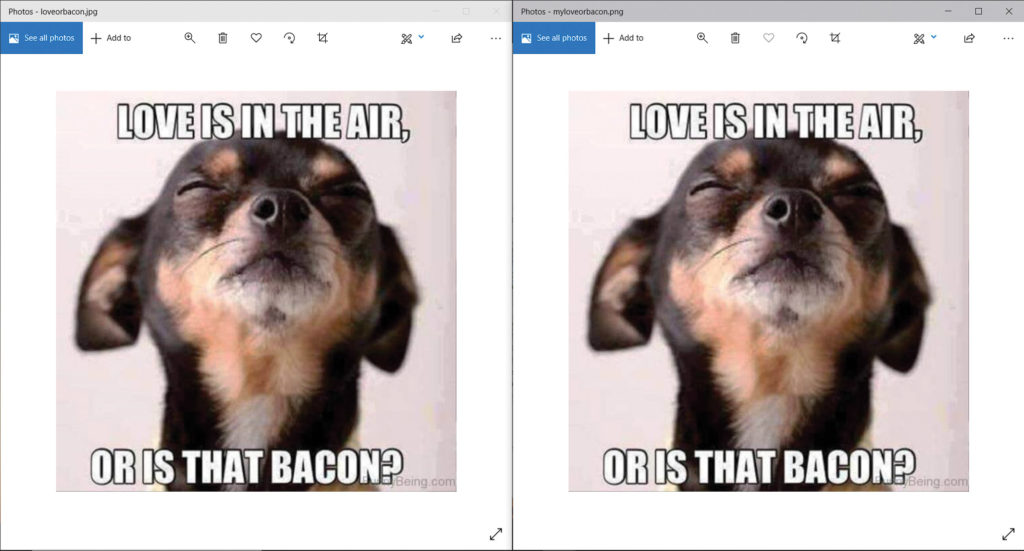
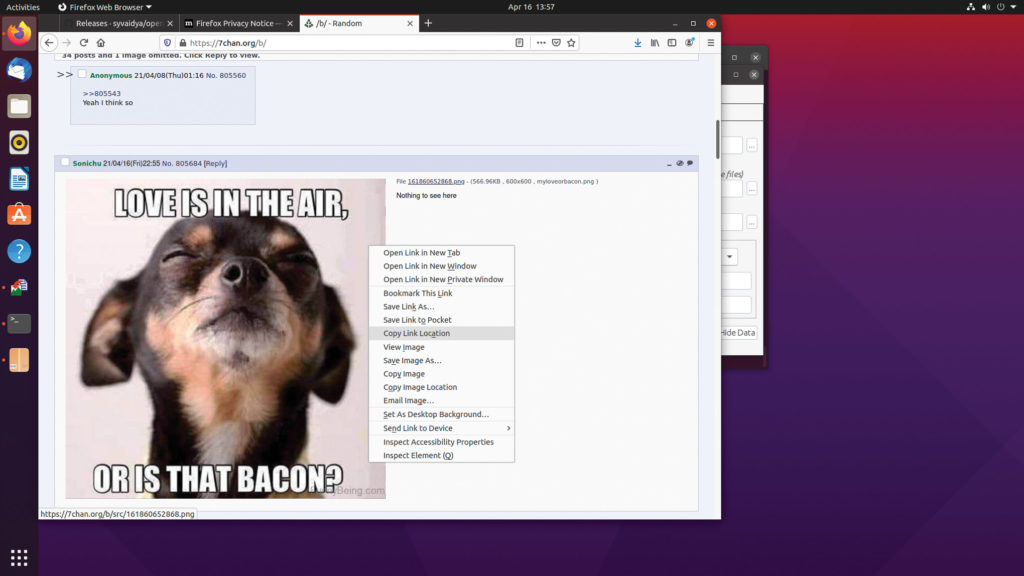
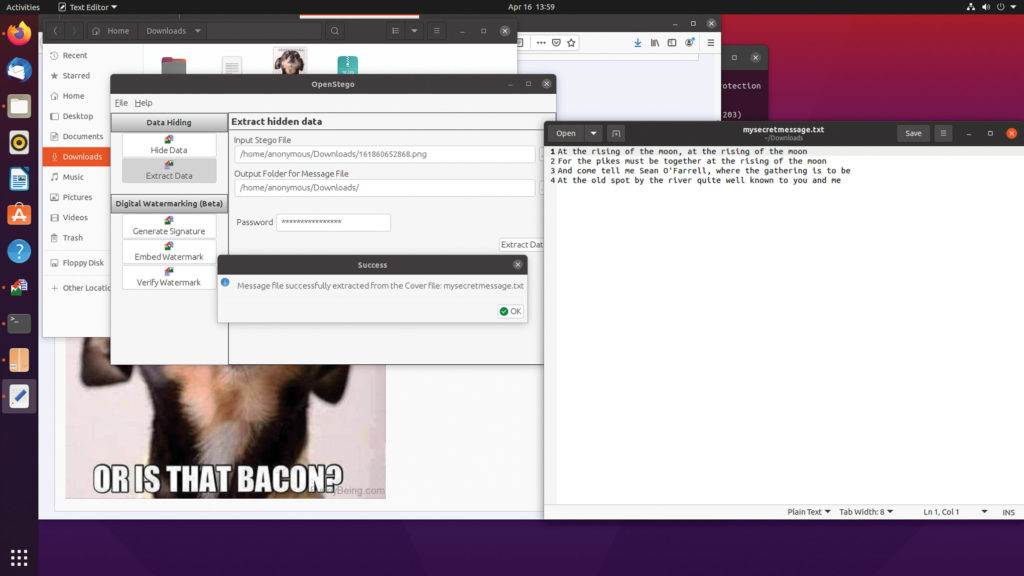

 Above: Hiding a message inside a raunchy “adult” photo may cause casual onlookers to click away in disgust, or deter them from visiting the type of sites that host that content in the first place.
Above: Hiding a message inside a raunchy “adult” photo may cause casual onlookers to click away in disgust, or deter them from visiting the type of sites that host that content in the first place.

































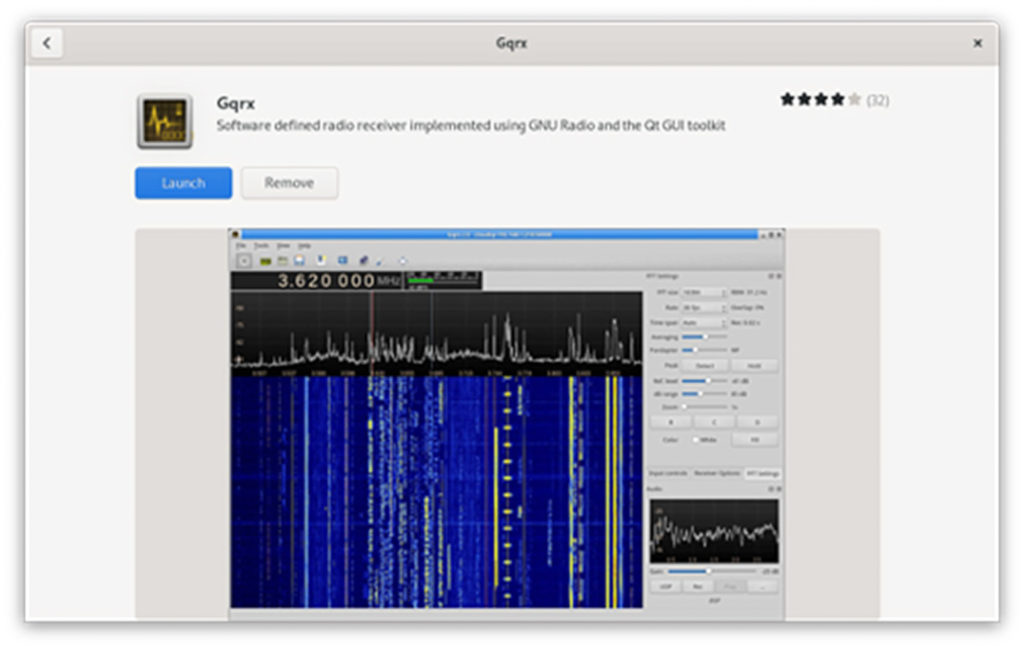
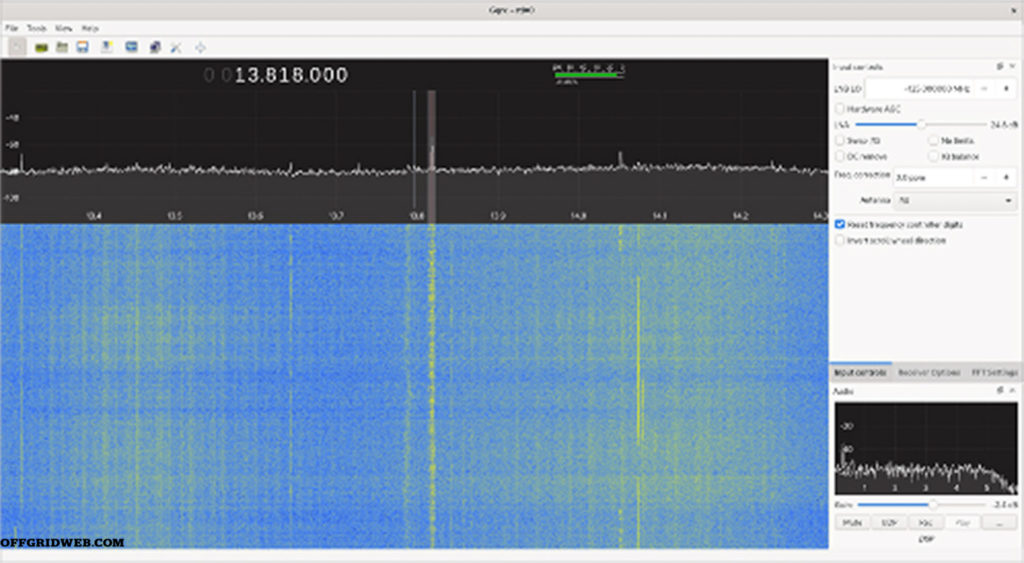
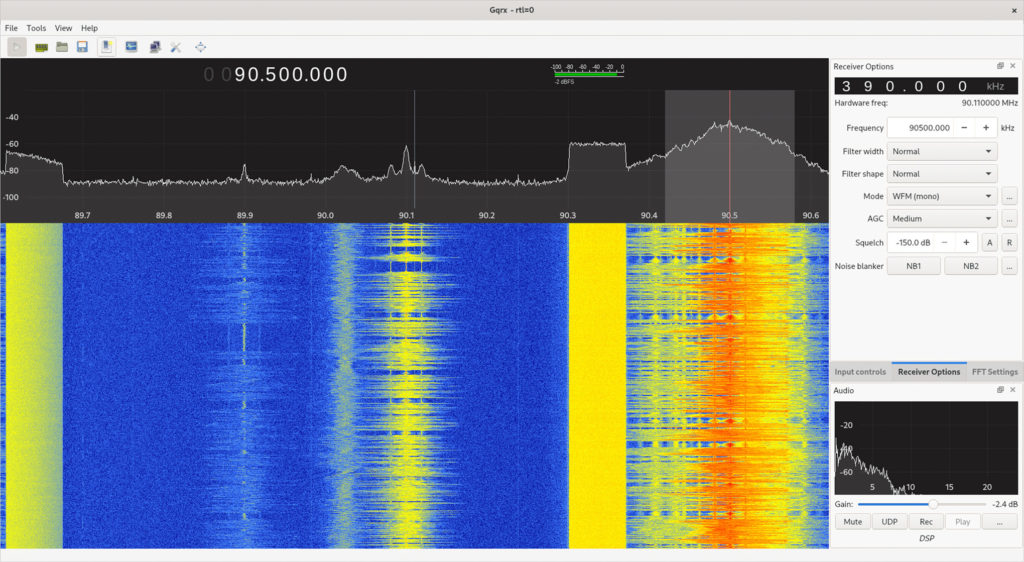 Above: Gqrx provides a waterfall display to show signal intensity (X-axis) over time (Y-axis), with color indicating signal strength. Here, we see the waterfall display for some broadcast FM stations in the Austin, Texas, area. Note that the mode is set to Wide FM.
Above: Gqrx provides a waterfall display to show signal intensity (X-axis) over time (Y-axis), with color indicating signal strength. Here, we see the waterfall display for some broadcast FM stations in the Austin, Texas, area. Note that the mode is set to Wide FM.
 Above: The Nooelec RTL-SDR bundle is a common, inexpensive way to get into SDR, including the ability to access HF bands with the Ham It Up up-converter. Depending on the antenna you want to use, you may need different cables.
Above: The Nooelec RTL-SDR bundle is a common, inexpensive way to get into SDR, including the ability to access HF bands with the Ham It Up up-converter. Depending on the antenna you want to use, you may need different cables.