RECOIL OFFGRID Preparation Digital Security: How to Set Up a VPN
In This Article
Like it or not, the Internet has dramatically changed the way we live our lives. These days, almost all of us use the web to pay bills, conduct important business transactions, and communicate with friends and family. Our photos are backed up on remote servers in the cloud, our social media likes and dislikes are recorded for marketing purposes, and our credit card transactions are conducted through web sites we can only assume are secure.
Some embrace this technology wholeheartedly, while others see it as a necessary evil—we all know it's a fact of life.

The days of physical storage media are coming to an end, and information is becoming available anywhere via the cloud.
However, this personal and sensitive information is increasingly at risk, due to both criminal attacks and potential government surveillance. You don't need a tinfoil hat these days to realize the need for practical information security. You may think that you're not important enough to be at risk, but security solely through obscurity is no security at all, especially when it comes to using the Internet.

This brings us to the topic of the VPN, short for Virtual Private Network. Using a VPN is one of the leading ways to retain your privacy online. It won't protect against every security vulnerability—it can't stop users from sharing their data with fraudsters or posting valuable info on social media, for example—but it's certainly a great place to start.
Fortunately, you don't need to be tech-savvy to understand VPNs, and we're going to prove that point by explaining the service here in layman's terms. If you're able to use a computer, browse the web, send emails, and read this article, you'll be able to set up a VPN quite easily.
Disclaimer: While using a VPN to protect your privacy is legal in most places (including the USA), you should check your local laws before setting up a VPN. Also, this information is provided for educational purposes only, and we are not responsible if you choose to do anything illegal with this knowledge. Be responsible, and recognize that a VPN cannot always provide foolproof protection in every circumstance.
So, what the heck is a Virtual Private Network? Good question. A VPN is a service that creates a secure Internet connection by encrypting your data and routing it through a secure private network. That sounds complicated, but think of it like this:
Let's say you live in a house in New York, and your friend lives in another house in California. To get to his house, you'll need to drive on public streets and highways. You can take any number of different paths, but you're still out in public, and someone could theoretically follow you or ambush you during your journey.
This is essentially how the Internet works—it's a network of information superhighways, but it's also accessible to anyone. You can take various measures to protect yourself (i.e. locking the doors on your car or leaving in the middle of the night) but you're vulnerable because you're out in public. The odds of anything bad happening are fairly low, but you're still at risk, especially if you're carrying valuables.
Now, let's say you build a secret underground tunnel all the way from your house to your friend's house. Not only that, but you install locked blast doors on each end of the tunnel, and exchange keys only with each other. Now, if you enter the underground tunnel to get to your friend's house, and lock the door behind you, no one will be able to follow or intercept you on your journey.

VPNs are often referred to as “tunnels” since they provide hidden pathways for data across networks.
This is how a VPN works. It protects you by routing you down a hidden private tunnel (obscurity), and also by locking that path so no one else can use it (encryption). Appropriately, VPNs are sometimes referred to as “tunnel servers”, because of this secretive nature.

Much like this 25-ton NORAD blast door, breaking through modern 2048-bit encryption is virtually impossible.
If you think of your house in this analogy as a computer, and your car as sensitive data (such as an email or bank transaction), you'll understand how using a VPN can protect you. Your computer exchanges trusted “handshake” encryption keys with another computer or VPN server, allowing you to securely and anonymously navigate the entire Internet via your encrypted VPN “tunnel”.
In case you were wondering, it's estimated that cracking a VPN's 2048-bit RSA encryption key using an ordinary desktop computer would take 4.6 quadrillion years of continuous processing time. Even with 100 supercomputers, it would be virtually impossible for any third party or surveillance program to guess a VPN's encryption key through trial and error.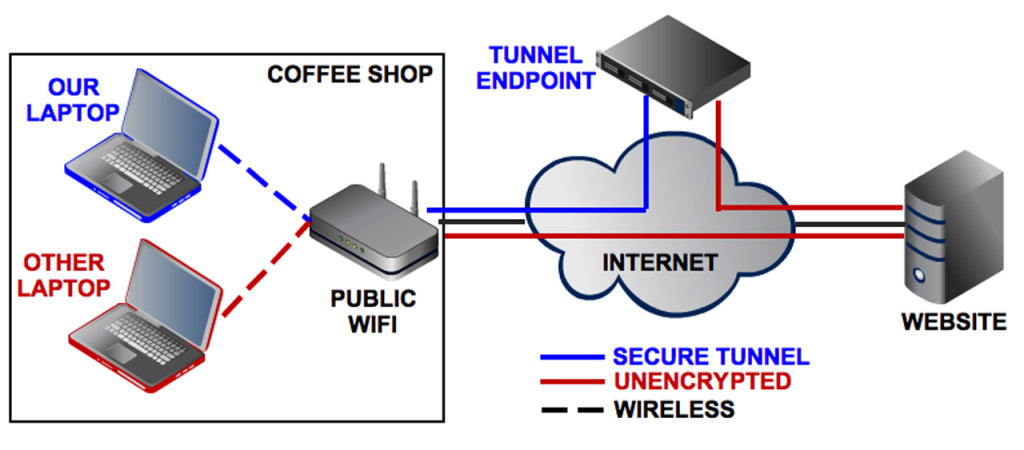
Now that you've heard our analogy, here's a concise diagram from PCWorld.com that shows how a VPN (the blue line) bypasses the mainstream Internet (the red line).
There are several benefits of using a VPN. Here's a quick breakdown of what a VPN can do for you:
Now that you know what a VPN does, and why it matters, you may want to take the leap and set up a VPN on your computer. First, you'll need to choose a VPN service provider.
Some VPN services are free, but we'd only recommend these if you're mostly concerned with bypassing country-based restrictions (benefit #3 above). For example, a free VPN can help you access regionally-restricted YouTube videos, streaming music services, and other geoblocked content. However, free VPNs are generally slower due to overcrowding, packed with ads, and much less secure than paid services. We'd advise you to avoid these, but here's a list of MostlyTech's Best Free VPN Services for 2016 if you'd like to do more research.
Aside from the inferior free options, you'll need to pay a small monthly fee to sign up for a VPN service. This fee usually ranges from $5 to $10 per month—a small price to pay for a massive amount of added privacy and security. We're not going to tell you which service to pick, but here are some guides that can help you choose:
Once you've chosen a VPN service, it's often as simple as downloading that service provider's application and installing it on your computer. For example, here's a guide from Private Internet Access that shows how to set up a VPN on a computer running Windows:
Seriously, it's that simple. Private Internet Access also offers an installer for Apple computers running Mac OS X, an iOS app for iPhones and iPads, and an Android app for other smartphones and tablets. There are dozens of providers that offer these same features, including TunnelBear, TorGuard, and WiTopia. Just choose the service that fits your needs and budget.
For more advanced users, it's possible to manually set up a VPN without installing any additional software. This can be useful if you're on a public or borrowed computer. Click here for a video guide for how to manually set up a VPN in Windows.
Digital security is of the utmost importance today, especially if you're a prepper or survivalist. You can lock down your house and take every precaution to physically safeguard your family, but if you leave your computer unprotected, you might as well be bolting the front door while leaving a window wide open.
Fortunately, as we've shown, you can set up a secure VPN to encrypt all your online transactions and activities for under $10 a month. Seems like an easy choice to us.
 STAY SAFE: Download a Free copy of the OFFGRID Outbreak Issue
STAY SAFE: Download a Free copy of the OFFGRID Outbreak Issue
No Comments